
by Stephen Crim | Mar 15, 2019 | Aquila inSecurity
When I talk about sensor-based products, what I’m specifically referring to is any product that sits outside of the traffic flow, and consumes network traffic either via a TAP/SPAN port, a packet broker or a switch with packet broker capabilities, or through...
by Damien Davies | Mar 8, 2019 | Aquila inSecurity
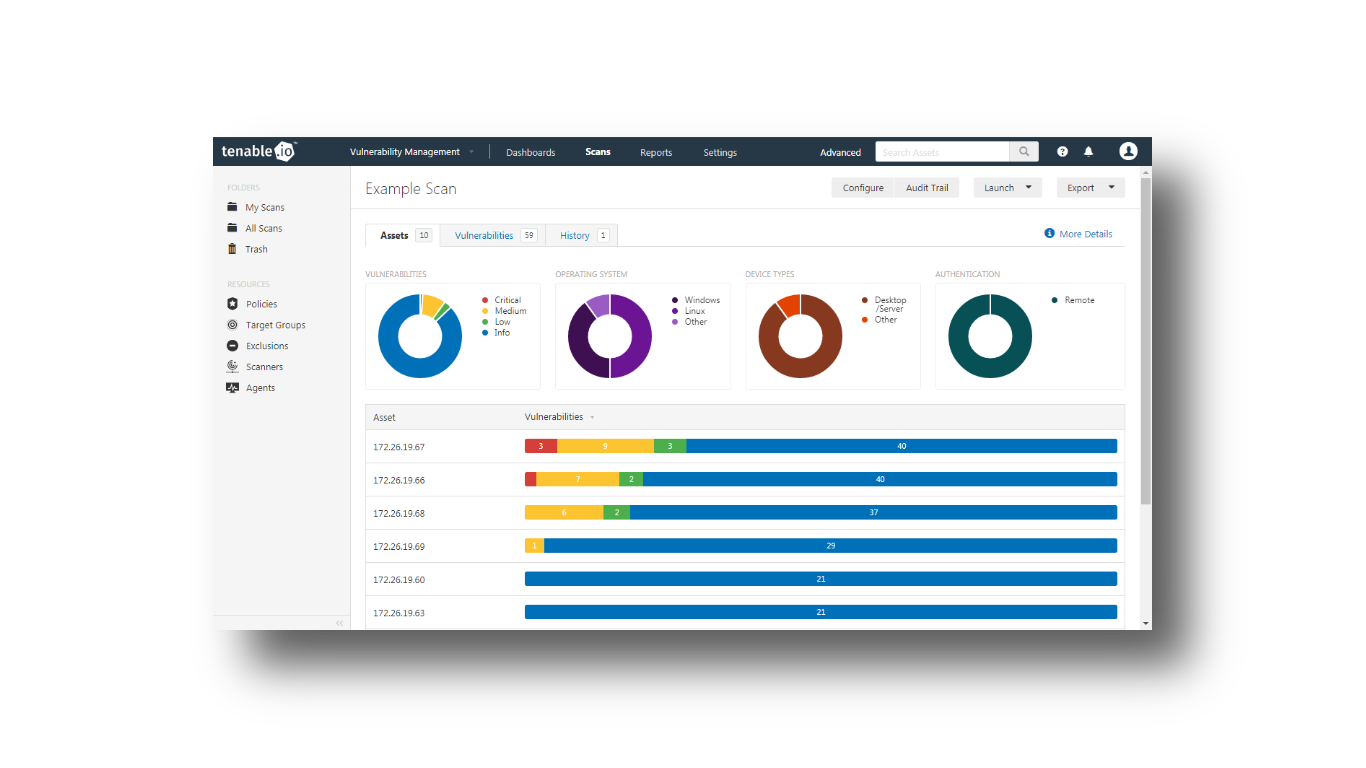
As an account manager, it is important to me that the solutions I partner with address three significant issues. The first of these is the issue of vulnerability. I am always on the hunt to find solutions that are at the cutting edge of protecting our customers’...

by Cody Jackson | Feb 27, 2019 | Aquila inSecurity
One of the key areas we can automate our defensive posture is understanding how the network we are defending looks. One of my SANS instructors once said: “you cannot protect what you don’t know about.” At the time I was working for an organization that had 12,000+...

by Cody Jackson | Feb 14, 2019 | Aquila inSecurity
Cybersecurity is an ever-increasing and advancing arms race. The attackers and threat actors are constantly harnessing new technology and techniques to increase their return on investment. As the defenders of our corporate, public, and private networks, we must do the...
by Cody Jackson | Feb 6, 2019 | Aquila inSecurity
APIs (Application Programming Interface) have become an increasingly important tool in IT. As businesses have become more reliant on connecting their business applications with each other and third-party tools a weak point has emerged in IT infrastructure. An...

by Stephen Crim | Jan 30, 2019 | Aquila inSecurity
Armis Breaks Down Vulnerabilities in the Internet of Things IoT (Internet of Things) has been the buzzword in security for the last 18 months. There have been a number of high-visibility breaches that were orchestrated because of them (one involving a wifi-connected...







