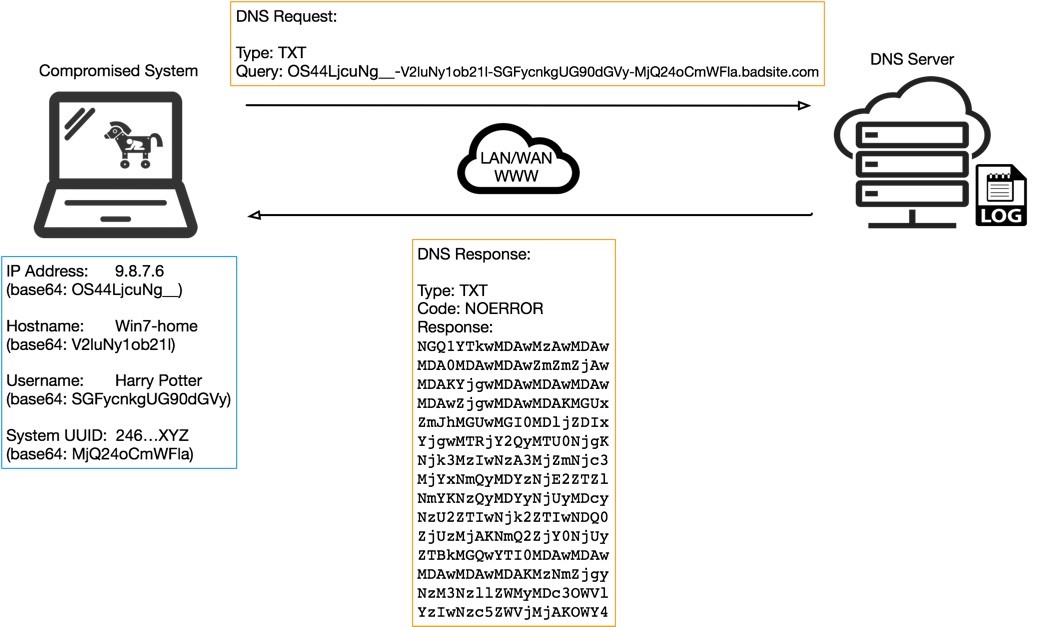
I stumbled on this excellent technical explanation of a relatively old data exfil method, using DNS tunneling. Many of us who have been enthusiasts of subverting systems going back to the 1980s have probably read ways to use exploit DNS to access the internet on dial-up ISP’s without authenticating.
https://unit42.paloaltonetworks.com/dns-tunneling-how-dns-can-be-abused-by-malicious-actors/
The only reason I bring this up is that it’s a great example of the type of vulnerability that can be caught with robust reporting and monitoring. DNS is one of those protocols that most people don’t consider a threat vector, but I rely on it for broad network behavior analysis all the time. While many edge firewalls can now record each query coming through, since DNS is such a simple protocol, I see many organizations ignore DNS logs on their Domain Controllers. This can obscure internal hosts who are relying on your DC’s for name resolution. You see the queries, but you don’t see the internal host that made the query, only the domain controller.

My best advice for these types of things is to invest the time in developing a process that makes it easy to review internal DNS service events. At the very least, the goal should be to make it easy enough to be casually curious about some DNS activity and get answers about the internal hosts responsible for it. A small investment in Splunk licensing can provide this kind of visibility, or other more purpose-built SEIM’s, but this could be as simple as an MMC console that gets you within a few clicks away from those answers.
If you do have it going into a SEIM, make sure you can quickly access dashboards that give you solid graphics and top talkers to at a glance notice aberrant behavior. Another tactic I’ve used is to use IP reputations to filter out everything that is known legit and everything that is known bad, and only report on the grey-scored activity. This is where the sneaky stuff will be, and we can focus more careful consideration on this information without being distracted by what we know is good and what we know is bad.
Happy hunting, and see you next week.
- How DNS Tunneling Can Be Abused - March 21, 2019
- The Rise of Sensor-Based Security Products - March 15, 2019
- Armis Breaks Down Vulnerabilities in the Internet of Things - January 30, 2019